拓扑图
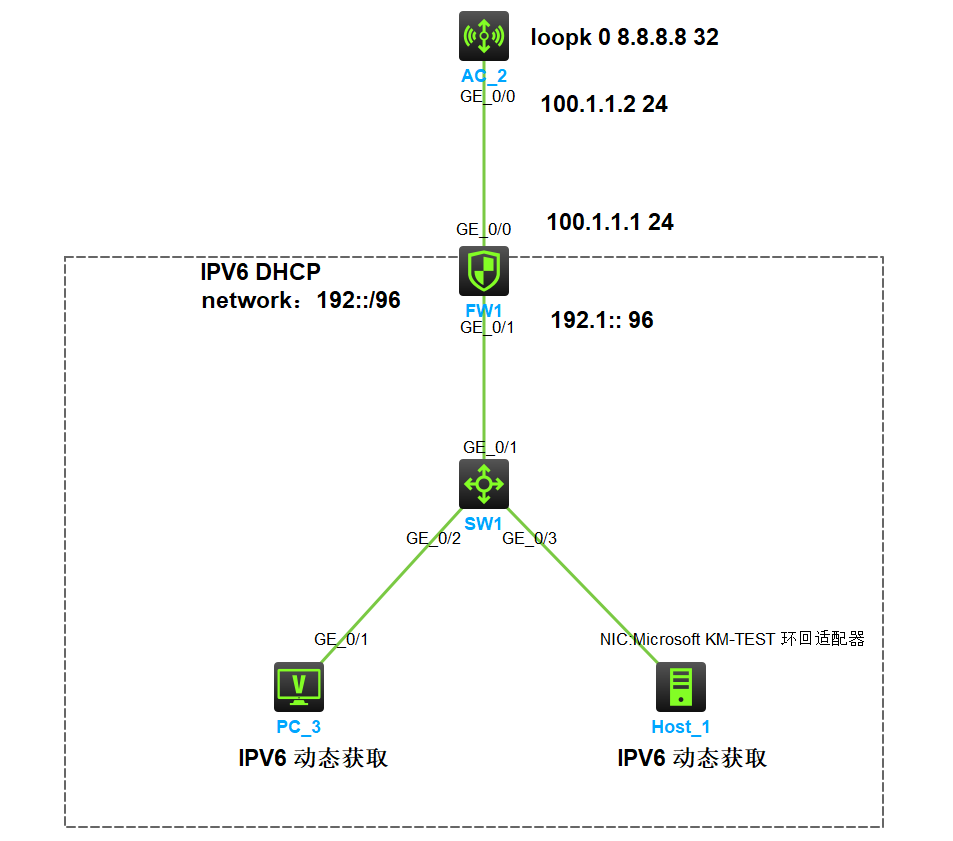
说明:sw1 为普通的二层交换机;FW1 防火墙做 IPV6 DHCP 为局域网的pc分配至ipv6地址。AC_2 上有一个 loopk 接口地址地址为 8.8.8.8 模拟公网的一台服务器,内网为 ipv6 外网为 ipv4
需求:需要内网的局域网的用户访问可以正常访问公网的 AC_2 8.8.8.8
配置步骤
基础配置(配置IP地址,路由,ipv6-dhcp, 配置安全策略)
接口加入安全域
[FW1]security-zone name Trust
[FW1-security-zone-Trust] import interface GigabitEthernet1/0/1
[FW1-security-zone-DMZ]security-zone name Untrust
[FW1-security-zone-Untrust] import interface GigabitEthernet1/0/0
配置安全策略
[FW1]security-policy ipv6
[FW1-security-policy-ipv6] rule 1 name aft-v6
[FW1-security-policy-ipv6-1-aft-v6] action pass
[FW1-security-policy-ipv6-1-aft-v6] source-zone Trust
[FW1-security-policy-ipv6-1-aft-v6] destination-zone Local
[FW1-security-policy-ipv6-1-aft-v6] source-ip-subnet 192::/96
[FW1-security-policy-ipv6-1-aft-v6] destination-ip-subnet 100::/96
[FW1-security-policy-ipv6-1-aft-v6] rule 0 name ipv6-dhcp
[FW1-security-policy-ipv6-0-ipv6-dhcp] action pass
[FW1-security-policy-ipv6-0-ipv6-dhcp] source-zone Local
[FW1-security-policy-ipv6-0-ipv6-dhcp] source-zone Trust
[FW1-security-policy-ipv6-0-ipv6-dhcp] destination-zone Trust
[FW1-security-policy-ipv6-0-ipv6-dhcp] destination-zone Local
[FW1]security-policy ip
[FW1-security-policy-ip] rule 2 name aft-v4
[FW1-security-policy-ip-2-aft-v4] action pass
[FW1-security-policy-ip-2-aft-v4] source-zone Local
[FW1-security-policy-ip-2-aft-v4] destination-zone Untrust
[FW1-security-policy-ip-2-aft-v4] source-ip-host 100.1.1.1
配置IP地址
[FW1]interface GigabitEthernet1/0/0
[FW1-GigabitEthernet1/0/0] port link-mode route
[FW1-GigabitEthernet1/0/0] ip address 100.1.1.1 255.255.255.0
[FW1-GigabitEthernet1/0/0]interface GigabitEthernet1/0/1
[FW1-GigabitEthernet1/0/1] ipv6 address 192::1/96
[AC-LoopBack0] ip address 8.8.8.8 255.255.255.255
[AC-LoopBack0]interface Vlan-interface1
[AC-Vlan-interface1] ip address 100.1.1.2 255.255.255.0
配置路由
[FW1] ip route-static 0.0.0.0 0 100.1.1.2
配置 IPV6 dhcp
[FW1]ipv6 dhcp pool 1
[FW1-dhcp6-pool-1] network 192::/96
[FW1-dhcp6-pool-1]qu
[FW1]interface GigabitEthernet1/0/1
[FW1-GigabitEthernet1/0/1] ipv6 dhcp select server
[FW1-GigabitEthernet1/0/1] ipv6 nd autoconfig managed-address-flag
[FW1-GigabitEthernet1/0/1] ipv6 nd autoconfig other-flag
[FW1-GigabitEthernet1/0/1] undo ipv6 nd ra halt
通过 dis ipv6 dhcp server ip-in-use 命令查看IPV6-DHCP地址分配情况
[FW1]dis ipv6 dhcp server ip-in-use
Pool: 1
IPv6 address Hardware address Type Lease expiration
192::2 0200-4c4f-4f50 Auto(C) Jan 20 15:39:23 2024
192::3 78b2-38bd-0306 Auto(C) Jan 20 16:29:45 2024
配置 AFT
[FW1]acl ipv6 basic 2000
[FW1-acl-ipv6-basic-2000] rule 0 permit source 192::/96 局域网下的哪些 IPV6 地址允许被转换成 IPV4
[FW1]aft address-group 1
[FW1-aft-address-group-1] address 100.1.1.1 100.1.1.1 局域网下的哪些 IPV6 地址可以被允许转换成哪些 IPV4 地址
[FW1]aft v6tov4 source acl ipv6 number 2000 address-group 1 把局域网下的哪些 IPV6 地址通过nat 64 前缀转换为 ipv4 地址(动态转换)
[FW1]aft prefix-nat64 100:: 96 当 ipv6 100::的前缀为 96 就会触发 aft
[FW1]interface GigabitEthernet1/0/0
[FW1-GigabitEthernet1/0/0] aft enable
[FW1-GigabitEthernet1/0/0]interface GigabitEthernet1/0/1
[FW1-GigabitEthernet1/0/1] aft enable
通过在PC_3测试
<H3C>ping ipv6 100::8.8.8.8
Ping6(56 data bytes) 192::3 --> 100::808:808, press CTRL_C to break
56 bytes from 100::808:808, icmp_seq=0 hlim=254 time=2.942 ms
56 bytes from 100::808:808, icmp_seq=1 hlim=254 time=2.288 ms
56 bytes from 100::808:808, icmp_seq=2 hlim=254 time=2.614 ms
56 bytes from 100::808:808, icmp_seq=3 hlim=254 time=2.297 ms
56 bytes from 100::808:808, icmp_seq=4 hlim=254 time=2.669 ms
查看 AFT 会话
[FW1]dis aft session ipv4 verbose
Slot 1:
Initiator:
Source IP/port: 100.1.1.1/11
Destination IP/port: 8.8.8.8/2048
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: ICMP(1)
Inbound interface: GigabitEthernet1/0/1
Source security zone: Local
Responder:
Source IP/port: 8.8.8.8/11
Destination IP/port: 100.1.1.1/0
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: ICMP(1)
Inbound interface: GigabitEthernet1/0/0
Source security zone: Untrust
State: ICMP_REPLY
Application: ICMP
Rule ID: 2
Rule name: aft-v4
Start time: 2023-12-21 16:45:18 TTL: 26s
Initiator->Responder: 0 packets 0 bytes
Responder->Initiator: 0 packets 0 bytes
Total sessions found: 1
[FW1]
[FW1]dis aft session ipv6 verbose
Slot 1:
Initiator:
Source IP/port: 192::3/500
Destination IP/port: 100::808:808/32768
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: IPV6-ICMP(58)
Inbound interface: GigabitEthernet1/0/1
Source security zone: Trust
Responder:
Source IP/port: 100::808:808/500
Destination IP/port: 192::3/33024
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: IPV6-ICMP(58)
Inbound interface: GigabitEthernet1/0/0
Source security zone: Local
State: ICMPV6_REPLY
Application: ICMP
Rule ID: -/-/-
Rule name:
Start time: 2023-12-21 16:45:18 TTL: 23s
Initiator->Responder: 0 packets 0 bytes
Responder->Initiator: 0 packets 0 bytes
Total sessions found: 1
