IPV4 访问 IPV6公网
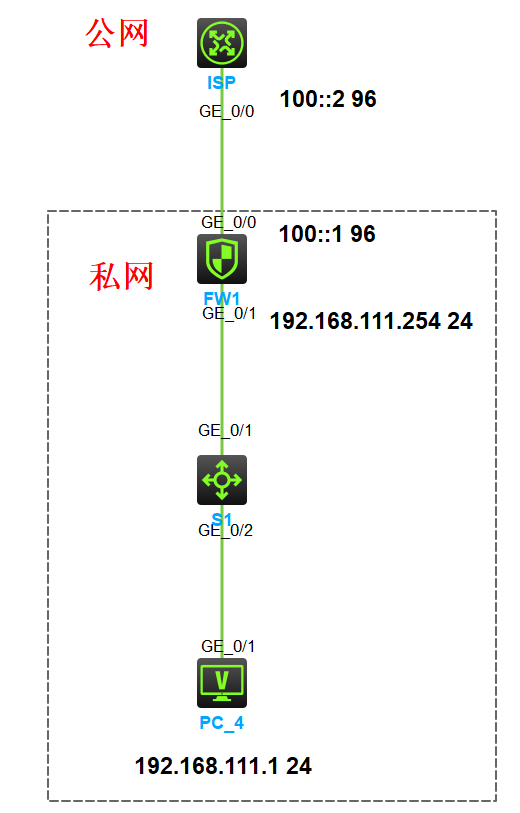
说明:
局域网为IPV4 网络但是公网已经改造为了IPv6 的网络此时。IPV4 是没有办法直接访问 IPV6 从而诞生出了 AFT (ipv4 到 IP v6 的过度技术)
AFT 的转换方式分为了:动态,静态,前缀转换
静态转换:由于一个IPv6 地址和一个 IPV4 地址进行一对一的映射。
动态转换:创建一个ipv6地址和一个IPV4 的对应起来但是转换的地址不是一一对应
前缀转换分为了:NAT64前缀转换、IVI前缀转换和General前缀转换。
本章使用的为 NAT 64前缀转换
实验要求:PC4 可以直接访问 ISP 的 ipv6 地址
基础配置(配置IP地址以及路由)
配置地址
[FW1]interface GigabitEthernet1/0/0 [FW1-GigabitEthernet1/0/0] aft enable [FW1-GigabitEthernet1/0/0] ipv6 address 100::1/96 [FW1-GigabitEthernet1/0/0]interface GigabitEthernet1/0/1 [FW1-GigabitEthernet1/0/1] ip address 192.168.111.254 255.255.255.0 [FW1-GigabitEthernet1/0/1] aft enable [ISP]interface GigabitEthernet0/0 [ISP-GigabitEthernet0/0] ipv6 address 100::2/96
配置路由
[ISP] ipv6 route-static :: 0 100::1
接口加入安全域
[FW1]security-zone name Trust [FW1-security-zone-Trust] import interface GigabitEthernet1/0/1 [FW1-security-zone-DMZ]security-zone name Untrust [FW1-security-zone-Untrust] import interface GigabitEthernet1/0/0
配置安全策略
[FW1]security-policy ip [FW1-security-policy-ip] rule 1 name aftlocal [FW1-security-policy-ip-1-aftlocal] action pass [FW1-security-policy-ip-1-aftlocal] source-zone Trust [FW1-security-policy-ip-1-aftlocal] destination-zone Local [FW1-security-policy-ip-1-aftlocal] source-ip-subnet 192.168.111.0 255.255.255.0 [FW1-security-policy-ip-1-aftlocal] destination-ip-host 20.1.1.1 [FW1]security-policy ipv6 [FW1-security-policy-ipv6] rule 1 name aftlocal-ipv6 [FW1-security-policy-ipv6-1-aftlocal-ipv6] action pass [FW1-security-policy-ipv6-1-aftlocal-ipv6] source-zone Local [FW1-security-policy-ipv6-1-aftlocal-ipv6] destination-zone Untrust [FW1-security-policy-ipv6-1-aftlocal-ipv6] source-ip-subnet 200::/96 [FW1-security-policy-ipv6-1-aftlocal-ipv6] destination-ip-host 100::2
配置 aft 功能
[FW1]acl basic 2000 [FW1-acl-ipv4-basic-2000] rule 0 permit source 192.168.111.0 0.0.0.255 只有 192.168.111.0 24 的IPV4 地址可以转换 [FW1-acl-ipv4-basic-2000] rule 5 deny [FW1] aft prefix-nat64 200:: 96 当匹配上前缀为 200:: 96 就会触发转换 [FW1] aft v4tov6 source acl number 2000 prefix-nat64 200:: 96 把acl 2000 的IPV4的源地址根据NAT64前缀转换为IPv6地址(动态转换) [FW1] aft v6tov4 source 100::2 20.1.1.1 将IPv6到IPv4的源地址进行静态转换,也可以将报文的目的地址转换为IPV4 对应的IPv6地址。
PC4测试
<H3C>ping 20.1.1.1 Ping 20.1.1.1 (20.1.1.1): 56 data bytes, press CTRL_C to break 56 bytes from 20.1.1.1: icmp_seq=0 ttl=63 time=4.615 ms 56 bytes from 20.1.1.1: icmp_seq=1 ttl=63 time=2.838 ms 56 bytes from 20.1.1.1: icmp_seq=2 ttl=63 time=2.546 ms 56 bytes from 20.1.1.1: icmp_seq=3 ttl=63 time=2.038 ms 56 bytes from 20.1.1.1: icmp_seq=4 ttl=63 time=2.635 ms
查看 AFT 会话通过 dis aft session ipv4/IPV6 verbose
[FW1]dis aft session ipv4 verbose Slot 1: Initiator: Source IP/port: 192.168.111.1/189 Destination IP/port: 20.1.1.1/2048 DS-Lite tunnel peer: - VPN instance/VLAN ID/Inline ID: -/-/- Protocol: ICMP(1) Inbound interface: GigabitEthernet1/0/1 Source security zone: Trust Responder: Source IP/port: 20.1.1.1/189 Destination IP/port: 192.168.111.1/0 DS-Lite tunnel peer: - VPN instance/VLAN ID/Inline ID: -/-/- Protocol: ICMP(1) Inbound interface: GigabitEthernet1/0/0 Source security zone: Local State: ICMP_REPLY Application: ICMP Rule ID: -/-/- Rule name: Start time: 2023-12-21 14:26:48 TTL: 23s Initiator->Responder: 0 packets 0 bytes Responder->Initiator: 0 packets 0 bytes Total sessions found: 1 [FW1]dis aft session ipv6 verbose Slot 1: Initiator: Source IP/port: 200::C0A8:6F01/189 Destination IP/port: 100::2/32768 VPN instance/VLAN ID/Inline ID: -/-/- Protocol: IPV6-ICMP(58) Inbound interface: GigabitEthernet1/0/1 Source security zone: Local Responder: Source IP/port: 100::2/189 Destination IP/port: 200::C0A8:6F01/33024 VPN instance/VLAN ID/Inline ID: -/-/- Protocol: IPV6-ICMP(58) Inbound interface: GigabitEthernet1/0/0 Source security zone: Untrust State: ICMPV6_REPLY Application: ICMP Rule ID: 0 Rule name: c Start time: 2023-12-21 14:26:48 TTL: 21s Initiator->Responder: 0 packets 0 bytes Responder->Initiator: 0 packets 0 bytes Total sessions found: 1 [FW1]