防火墙安全域+安全策略 (基础 HCL实验)
实验须知:1:了解同一区域内互访安全规则,掌握安全策略配置
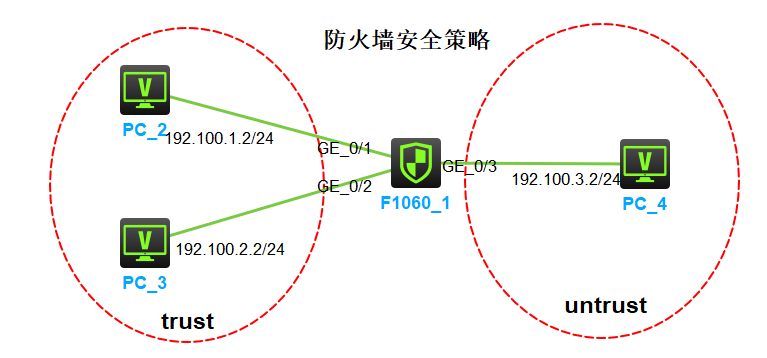
配置步骤
1、防火墙进入,用户名密码 admin/admin ,配置IP地址;
Press ENTER to get started. Login: admin Password: [H3C]sysname FW [FW]interface g1/0/1 [FW-GigabitEthernet1/0/1]ip address 192.100.1.1 24 [FW-GigabitEthernet1/0/1]int g1/0/2 [FW-GigabitEthernet1/0/2]ip address 192.100.2.1 24 [FW-GigabitEthernet1/0/2]int g1/0/3 [FW-GigabitEthernet1/0/3]ip address 192.100.3.1 24
2、防火墙接口接口加入安全域(防火墙上的接口必须要在安全域里,接口加入 用 ‘’import‘' 命令)
[FW]security-zone name Trust [FW-security-zone-Trust]import int g1/0/1 [FW-security-zone-Trust]import int g1/0/2 [FW]security-zone name Untrust [FW-security-zone-Untrust]import interface g1/0/3
3:开启接口服务功能(新版本接口下可以直接开启,分为两个方向,根据自己需求选择,功能也是需要那个开通那个)
[FW-GigabitEthernet1/0/1]manage ping inbound //开启g1/0/1 接口功能 [FW-GigabitEthernet1/0/1]manage ping outbound [FW-GigabitEthernet1/0/1]manage https inbound [FW-GigabitEthernet1/0/1]manage https inbound [FW-GigabitEthernet1/0/1]manage telnet inbound [FW-GigabitEthernet1/0/1]manage ssh inbound [FW-GigabitEthernet1/0/2]manage ping inbound //开启g1/0/2 接口功能 [FW-GigabitEthernet1/0/2]manage ping outbound [FW-GigabitEthernet1/0/3]manage ping inbound //开启g1/0/3接口功能 [FW-GigabitEthernet1/0/3]manage pin outbound
4、同一区域内互访(默认V7以上防火墙同一区域内也是禁止互访)
<PC2>ping 192.100.2.2 // PC2 ping 不通 PC3,同一区域内禁止访问 Ping 192.100.2.2 (192.100.2.2): 56 data bytes, press CTRL_C to break Request time out [FW] security-zone intra-zone default permit //开启允许同一区域内互访 [PC2] ping 192.100.2.2 Ping 192.100.2.2 (192.100.2.2): 56 data bytes, press CTRL_C to break 56 bytes from 192.100.2.2: icmp_seq=0 ttl=254 time=1.000 ms 56 bytes from 192.100.2.2: icmp_seq=1 ttl=254 time=0.000 ms
5:安全策略
[FW]security-policy ip //开启安全策略功能 [FW-security-policy-ip]rule name t-u //创建规则,name 必须要配置,建议按方向起名 [FW-security-policy-ip-0-t-u]source-zone trust //源区域, [FW-security-policy-ip-0-t-u]destination-zone untrust //目标区域 [FW-security-policy-ip-0-t-u]action pass //激活区域 [FW-security-policy-ip]rule name u-t //配置反方向的规则 [FW-security-policy-ip-1-u-t]source-zone untrust [FW-security-policy-ip-1-u-t]destination-zone trust [FW-security-policy-ip-1-u-t]action pass [PC2]ping 192.100.3.2 Ping 192.100.3.2 (192.100.3.2): 56 data bytes, press CTRL_C to break 56 bytes from 192.100.3.2: icmp_seq=0 ttl=254 time=1.000 ms 56 bytes from 192.100.3.2: icmp_seq=1 ttl=254 time=1.000 ms 56 bytes from 192.100.3.2: icmp_seq=2 ttl=254 time=1.000 ms